Technology
6/recent/technology
Showing posts with the label protectShow All
The Top 4 Brand Protection Strategies for 2018
First of imagine with customer idea across social network, web and different mobile apps. This Omni channel to grow network with complete engageme…
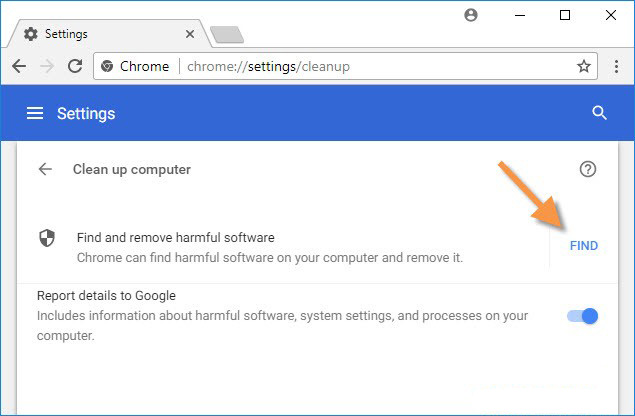
Read moreHow to Scan Your PC for Harmful Virus with Google Chrome
Google last summit to announce Google Chrome has become one of the quickest and rapidly popular in whole world. One of the main reason because Goo…
Read moreTop 8 GDPR Tips Must Need Every Business Entrepreneur
It means your entrepreneur or business needs to be ready to observe with General Data Protection Regulation (GDPR). This condition was approved by…
Read moreHow to Secure Your Desktop & PC from Ransomware Attacks
A decade-old pattern form of harmful software known as ransomware has been making breaking news after cyber-criminals attacked millions of compute…
Read moreAd Space
Popular Posts
Subscribe Us
Labels
Technology
3/Technology/post-list
Random Posts
3/random/post-list
Recent in Tech News
3/Technology/post-list
Popular Posts
Menu Footer Widget
Crafted with by TemplatesYard | Distributed by Gooyaabi Templates










Social Plugin