Technology
6/recent/technology
Showing posts with the label malwareShow All
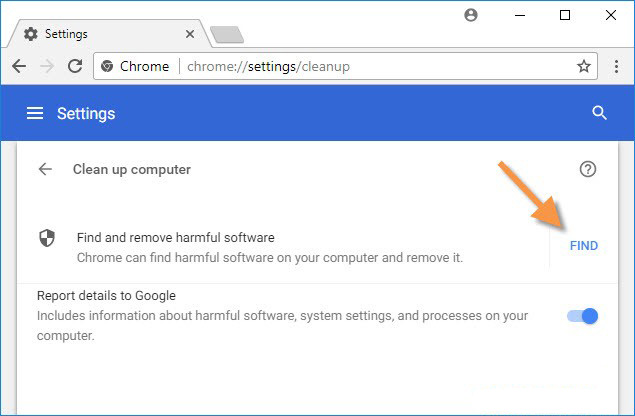
How to Scan Your PC for Harmful Virus with Google Chrome
Google last summit to announce Google Chrome has become one of the quickest and rapidly popular in whole world. One of the main reason because Goo…
Read moreHow to Secure Your Desktop & PC from Ransomware Attacks
A decade-old pattern form of harmful software known as ransomware has been making breaking news after cyber-criminals attacked millions of compute…
Read moreAd Space
Popular Posts
Subscribe Us
Labels
Technology
3/Technology/post-list
Random Posts
3/random/post-list
Recent in Tech News
3/Technology/post-list
Popular Posts
Menu Footer Widget
Crafted with by TemplatesYard | Distributed by Gooyaabi Templates








Social Plugin